The following are code examples for showing how to use cryptography.x509.randomserialnumber.They are extracted from open source Python projects. You can vote up the examples you like or vote down the ones you don't like. The sequence number guarantees that the serial number is unique within a replica, so there is no need for collision detection. The replica ID guarantees that the serial number is unique globally, so there is no need for a complex range assignment and switching mechanism. The serial numbers can be grouped by replica and can be sorted per replica. The serial number of the certificate is part of the original X.509 protocol. The serial number is a unique number issued by the certificate issuer, which is also called the Certificate Authority (CA).
Is certificate serial number a unique key for X509 certificate?User selects a certificate, and program stores serial number in preferences. Will the following code return the selected certificate?
UPDATE: I ended up using certificate thumbprint, as suggested by jglouie.
davmos4 Answers
No. For example, OpenSSL let's the user set this when they create certificates.
See: http://www.openssl.org/docs/apps/x509.html
-set_serial n specifies the serial number to use. This option can be used with either the -signkey or -CA options. If used in conjunction with the -CA option the serial number file (as specified by the -CAserial or -CAcreateserial options) is not used.
The serial number can be decimal or hex (if preceded by 0x). Negative serial numbers can also be specified but their use is not recommended.
jglouiejglouie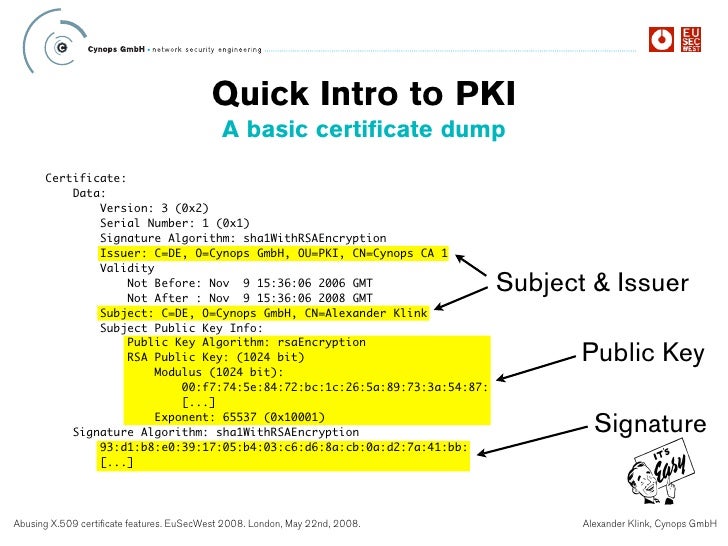
As mentioned in another answer, the serial number must be unique within the CA. So serial number alone can't be used as a unique ID of the certificate -- certificates from different CAs can have the same serial number. You need to store combination of Issuer and SerialNumber properties. Also, for self-signed certificates and home-made CA software numbers will most likely collide as many people will start numbering from 0.
Eugene Mayevski 'Allied BitsEugene Mayevski 'Allied BitsX 509 Certificate Serial Number Unique
Yes, according to X.509 specification serial number is unique for specific CA:
4.1.2.2 Serial number
The serial number is an integer assigned by the CA to each certificate. It MUST be unique for each certificate issued by a given CA (i.e., the issuer name and serial number identify a unique certificate).
OybekTL;DR: You must use a composite key of issuer name + serial number. If you need a simple key, use certificate's thumbprint.
Quoting @ThomasPornin from security.stackexchange:
In a certificate, the serial number is chosen by the CA which issued the certificate. It is just written in the certificate. The CA can choose the serial number in any way as it sees fit, not necessarily randomly (and it has to fit in 20 bytes). A CA is supposed to choose unique serial numbers, that is, unique for the CA. You cannot count on a serial number being unique worldwide; in the dream world of X.509, it is the pair issuerDN+serial which is unique worldwide (each CA having its own unique distinguished name, and taking care not to reuse serial numbers).
The thumbprint is a hash value computed over the complete certificate, which includes all its fields, including the signature. That one is unique worldwide, for a given certificate, up to the inherent collision resistance of the used hash function. Microsoft software tends to use SHA-1, for which some theoretical weaknesses are known, but no actual collision has been produced (yet).
From: https://security.stackexchange.com/questions/35691/what-is-the-difference-between-serial-number-and-thumbprint
Not the answer you're looking for? Browse other questions tagged c#x509certificateserial-number or ask your own question.
- About this Journal ·
- Abstracting and Indexing ·
- Aims and Scope ·
- Article Processing Charges ·
- Bibliographic Information ·
- Editorial Board ·
- Editorial Workflow ·
- Publication Ethics ·
- Reviewer Resources ·
- Submit a Manuscript ·
- Subscription Information ·
- Open Special Issues ·
- Published Special Issues ·
The Prediction of Serial Number in OpenSSL’s X.509 Certificate
1Institute of Information Engineering, Chinese Academy of Sciences, China
2School of Cyber Security, University of Chinese Academy of Sciences, China
3Shandong Provincial Key Laboratory of Computer Networks, Shandong Computer Science Center (National Supercomputer Center in Jinan), Shandong Academy of Sciences, China
4School of Cyber Security, Qilu University of Technology, China
Correspondence should be addressed to ; gro.sads@hzjgnaw
Received 14 November 2018; Accepted 25 March 2019; Published 2 May 2019
Academic Editor: A. Peinado
Copyright © 2019 Jizhi Wang. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Abstract
In 2007, a real faked X.509 certificate based on the chosen-prefix collision of MD5 was presented by Marc Stevens. In the method, attackers needed to predict the serial number of X.509 certificates generated by CAs besides constructing the collision pairs of MD5. After that, the randomness of the serial number is required. Then, in this case, how do we predict the random serial number? Thus, the way of generating serial number in OpenSSL was reviewed. The vulnerability was found that the value of the field “not before” of X.509 certificates generated by OpenSSL leaked the generating time of the certificates. Since the time is the seed of generating serial number in OpenSSL, we can limit the seed in a narrow range and get a series of candidate serial numbers and use these candidate serial numbers to construct faked X.509 certificates through Stevens’s method. Although MD5 algorithm has been replaced by CAs, the kind of attack will be feasible if the chosen-prefix collision of current hash functions is found in the future. Furthermore, we investigate the way of generating serial numbers of certificates in other open source libraries, such as EJBCA, CFSSL, NSS, Botan, and Fortify.
1. Introduction
Digital certificates are adopted widely in Internet, which is a basic security measurement. Many principals, such as clients and servers, depend on digital certificates to authenticate each other. If an attacker can forge other’s digital certificate, he/she may impersonate other’s identity and access sensitive information. This is one of serious threats for the public.
Kumpulan Serial Number Idm
The security of digital certificates is based on the digital signature algorithms and hash algorithms. If an attack against these algorithms occurs, the digital certificates based on these algorithms cannot be trusted any more. Among attacks, collision of hash algorithms is one of the most serious threats. Since the first real MD5 collision attack was presented by Wang [1, 2] in 2004, it is possible to construct forged certificates based on the collision attack of MD5.
At Eurocrypt 2007, the different certificates with the same signature were created firstly by Stevens based on the chosen-prefix collision attack of MD5 [3–5]. This was a big event for commerce CAs and their users because the kind of forged certificates can be verified successfully. After that, many companies announced that MD5 was vulnerable to digital certificates, such as Verisign, Microsoft, Mozilla, TC TrustCenter, RSA, US-CERT, and Cisco [6]. In addition, the super-malware Flame was discovered in 2012 [7], which uses the method to forge a Microsoft’s certificate [8].
The method of Stevens cannot forge a certificate from an existing certificate because the second preimage attack of MD5 is hard so far. The method needs to construct two certificates based on chosen-prefix collision attack of MD5 before submitting one of them to apply for a certificate to a CA. The implementation of the process has two key issues, one related to the collision pair construction of MD5 and the other to some fields controlled by CAs, such as serial number, in certificates, which attackers need to predict before submitting the application. Against the threat, Stevens gave two suggestions for CAs: one is to replace MD5 algorithm with other secure hash algorithms (such as SHA-256) because chosen-prefix collision of other hash algorithms does not occur at present; the other is to add a sufficient amount of fresh randomness at the appropriate fields (such as serial number) in order to prevent attackers from predicting if MD5 cannot be replaced at once [5]. In the wild, however, many valid certificates still use MD5 [9]. In addition, we grabbed 180,000+ certificates from Internet, while 5000+ certificates are based on MD5, in other words 2.8% certificates.
In this paper, we will focus on whether the randomness of some fields in certificates is enough to prevent attackers from predicting. Since the detailed codes of business CAs are not public, we review the way of generating certificates by open source software OpenSSL to find how to predict the values of some fields in certificates. OpenSSL uses a pseudo random number generator (PRNG) to output random numbers. Some literatures related to the security of the PRNG have been proposed [10–15]. The security of OpenSSL’s PRNG in Android and Debian has been reported in [10, 14]. A theory analysis of OpenSSL’s PRNG was presented in [10]. However, it is not clear how the PRNG works in the procedure of generating X.509 certificates. Furthermore, we also investigated generating certificates in other open source libraries, like EJBCA, CFSSL, NSS, Botan, and Fortify.
In this paper, we have three contributions as follows:(1)We find a vulnerability of OpenSSL that the field “not before” in certificates leaks the time of generating certificates, which is the seed of generating the field “serial number,” so that it is possible to predict the value of “serial number.”(2)We give the predicting method for the field “serial number” and forge certificates based on the proposed method and Stevens’s method.(3)We investigate five other open source libraries and find similar vulnerability in two libraries, EJBCA and NSS.
The paper is organized as follows. In Section 2, some preliminaries are introduced and the problems solved by the paper are defined. Section 3 reviews the source codes of OpenSSL about generating X.509 certificates. Then, Section 4 proposes a method predicting the key fields of certificates. Some countermeasures are given in Section 5 and Section 6 investigates other open source libraries. Finally, Section 7 concludes the paper.
2. Preliminaries
In X.509 certificates, the signature of CA is the most important part to prevent from forging. Any modification of contents in certificates would make the change of CA’s signature, in other words the change of Hash value. If a user A’s certificate has existed, we cannot forge the certificate directly because it needs to construct the second preimage of hash value of the certificate. However, we can use other user B’s identity to apply a certificate for CA, and generate a chosen-prefix collision pair, which can forge A’s certificate.
2.1. Chosen-Prefix Collision Attack of MD5
According to the chosen-prefix collision, the prefixes p and of two message blocks are chosen. Then, the collision pair, s and , is generated, so that is satisfied for any arbitrary suffix d. The two prefixes p and must be of equal length and their length is a multiple of the MD5 message block size. Otherwise, padding message must be added. The computing complexity of the attack is [4, 5] and a program was presented by Stevens [16]. For attackers, the method can be applied to forge certificates successfully.
Before that, identical-prefix collision had been studied, which is easier to be constructed than chosen-prefix collision. Although identical-prefix collision can be used to forge certificates, the kind of forgery is meaningless in practical attacks because the user’s identity is in the prefix and cannot be changed.
The overview of collision complexities is in Table 1. We can see the chosen-prefix collision of MD5 is feasible in computing while the chosen-prefix collision of SHA-1 is unfeasible so far. But, in the near future, a real case of chosen-prefix collision of SHA-1 may be found, when the attack will be feasible.